<>
What are Portal DB provider access privileges?
Related topics
Provider access privileges define the actions that can be performed
on a provider and the database portlets owned by it. By default, you are
granted the highest level of access, Manage access privilege, on any
provider you create. With Manage privileges, not only can you perform
actions on the provider and create database portlets within it, but you can
grant access privileges to other Portal developers. You can also
delete the provider.
The Action column of the
Portal Navigator indicates the actions you can perform on the
provider. (Actions not available to you are not listed.)
Provider-level versus database portlet-level privileges
Provider-level privileges potentially apply to all database portlets in an
provider. Any database portlet built in a provider inherits privileges by
default from the provider. For example, after MY_CHART is created in MY_APP, Oracle
Portal developers with Edit or higher access privileges on MY_APP
can edit MY_CHART.
database portlet-level privileges apply only to individual database portlets within
a provider. Users with Manage provider-level access can override
these privileges and set access on a database portlet level rather than the
provider level.
Provider-level access privileges and the actions you can perform with
them are listed below.
Provider-level access privileges
|
|
Manage |
Edit |
View Source |
Customize |
Execute |
|
Grant provider privileges to other users |
 |
|
|
|
|
|
Drop the provider and all of its
database portlets from the database. |
 |
|
|
|
|
|
Rename and export the provider |
 |
 |
|
|
|
|
Create database portlets in the provider |
 |
 |
|
|
|
|
Edit database portlets owned by the provider |
 |
 |
|
|
|
|
Drop individual database portlets owned
by the provider |
 |
 |
|
|
|
|
Copy, rename, and export database portlets owned by the provider |
 |
 |
|
|
|
|
View the call interface, package spec and body of database portlets owned by
the provider |
 |
 |
 |
|
|
|
Customize the provider or any database portlet within it |
 |
 |
 |
 |
|
|
Run the provider or any database portlet
within it |
 |
 |
 |
 |
 |
Development versus runtime privileges
The above privileges can be divided into those that apply to provider
development or to runtime provider deployment. MANAGE, EDIT, and VIEW
privileges provide security for a provider while it is being developed.
Because MANAGE privileges provide the ability to do anything in a
provider, you'd typically grant it to one or more project leads with
overall responsibility for planning and managing the development of
the provider.
EDIT privileges typically are granted to developers who will be
creating and updating the provider's database portlets.
VIEW SOURCE privileges might be granted to other developers who need
to know what the provider's code looks like, but don't need to edit
or add code. For example, you might grant this privilege to a shared
database portlet developer or a developer of another provider who is
creating a named link to a database portlet in your provider.
CUSTOMIZE and RUN privileges provide access to the provider after it
has been created and deployed in a run-time environment such as an
Oracle Portal content area. RUN enables a user to run any database portlet
in the provider,
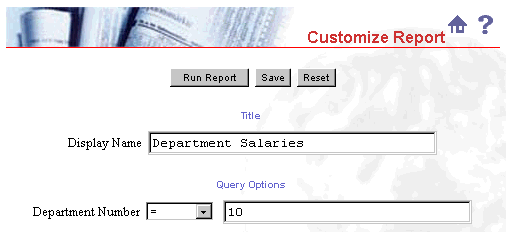
You can restrict access to a provider using CUSTOMIZE. For example,
you may want provide some users with a restricted view of salary
data, but allow other a wider view. You could include in your
provider a report that by default presents data for a particular
department. All users with RUN privileges could see that data. Users
with CUSTOMIZE privileges might customize the report to view data for
that department or other departments.
Related topics
Granting provider access privileges
Back to top
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
